
CategoryCrime


How One Woman’s Campaign Nearly Destroyed Pornhub
In 2020 it was the 10th most visited website on the internet, now just a shell of its former days
If Information Is Wealth, Are Deepfakes a Form of Counterfeiting?
The current tech media overdose on panic over deepfakes. They could be drowning out practical ways of fighting back
Will Deepfakes Be Used to “Show” Us That Computers Can Now Think?
As the deepfake technology advances, William Dembski wonders whether some AI zealots might try to “fake it till they make it,” Theranos-style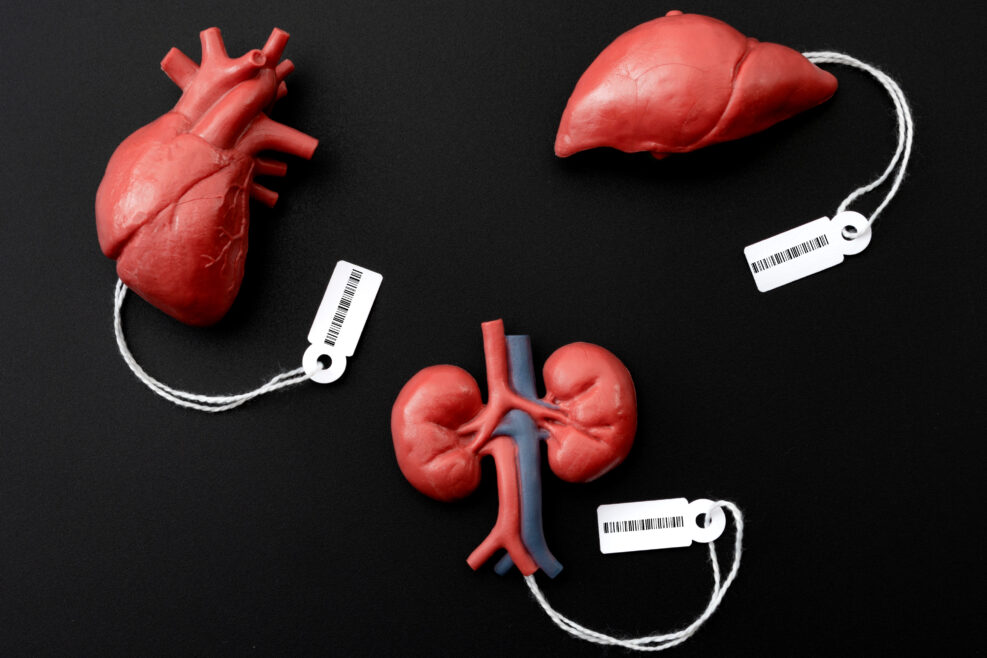
Organ Transplants: How the Internet Enables the Dark Side
Euthanasia activists offer to "ease" the donor organ shortage, and so do cartels that exploit the world’s most vulnerable poor
Twitter’s Censorship — Child Porn (Shrug… ), MDs’ Doubts: NO!
Twitter censored doctors and researchers who raised doubts about COVID strategies but seemed helpless about child pornEarlier this week, we looked at The Verge’s groundbreaking coverage of Twitter’s inability to prioritize and address child porn (and non-consensual nudity) at the site. One of the authors, Casey Newton, followed up Wednesday at Platformer,, filling readers in on new facts that he and Zoe Schiffer learned from a former Twitter employee after their story was published. One was that “Twitter’s move would draw Apple’s attention to the significant amount of porn on the service, and potentially place new restrictions on its iOS app or even remove it from the App Store.” That’s no idle threat, Newton reminds us. In 2018, Tumblr was dropped from the Apple app store when “child sexual abuse material (CSAM) was found on the Read More ›

Swatting Goes Into Politics — as Congresswoman Greene Discovered
Swatting — calling the police and pretending that a violent incident is taking place at a given address — can kill the victimThis has been a summer to remember for U.S. Congresswoman Marjorie Taylor Greene (R-Georgia). She was “swatted” twice. The first false report that brought the police to her home was Wednesday, August 23: According to the first Rome PD report, five officers responded to a call on Wednesday during the initial attempted swatting. The caller claimed that a man had been “shot five times in a bathtub” at Greene’s home, and there was a woman and possibly children still in potential danger. On the way to Greene’s house, police realized who the homeowner was, but “due to the nature of the call,” police “formed up” at a nearby intersection and made a “tactical approach.” Rome PD provided Ars with no Read More ›

What To Do If Your Business Is Hit With a Ransomware Demand
A roundup of advice for small businesses and their employees and contract workers, on site or remoteRansomware attacks have reportedly continued to grow in 2022, as criminals hone their skills in grabbing our data and wanting money to release it. Today, it’s not just government and large businesses that are at risk. Small to mid-size businesses are at greatest risk. That’s because a) they often don’t have enough security in place and b) let’s face it, today’s attacker might be content with $300,000 each from a cluster of them rather than $30 million from a giant firm. Attracts less attention, for one thing. Here’s Blackfog’s monthly list of publicly reported attacks in 2022. In the first 30 minutes… Don’t just panic and agree to pay: [Kevin] Epstein says international law enforcement and white hat hackers usually Read More ›

Deep Web? Dark Web? What’s Dangerous? What’s to Know?
The Deep Web hosts information like bank statements and health records so a search on your name won't turn them upThe terms deep and dark sound glamorous and forbidding, maybe criminal. Both terms just mean that we can’t reach a site on that portion of the web via a conventional search engine. The Surface Web, the part that we can reach via a conventional search engine like Google, DuckDuckGo, or Brave, is estimated roughly to be 0.03% of the internet (Britannica). The Deep Web contains email accounts, bank statements, health records, and other services that can only be accessed by passwords. It’s the main reason that our private business can’t be accessed just by searching on our names. Both the Surface Web and the Deep Web are growing as more people go online. Now, about the Dark Web: By comparison, Read More ›

Largest Data Grab Ever Stole Shanghai’s Mass State Surveillance
The police, dutiful in monitoring everyone, flunked data security. Now it’s all for sale on the Dark WebBeijing wants to create a centralized database with personal information on everyone living in China. To do that, the government saves massive amounts of data acquired through surveillance technologies such facial and voice recognition and cell phone monitoring. In a previous article, we saw that the Chinese government’s surveillance network is much more extensive than once thought. However, while the Chinese government has prioritized collecting massive amounts of data, it has not prioritized protecting it. Thus, a hacker has acquired police data files on 1 billion Chinese residents (approximately 23 terabytes of data) from the Shanghai National Police database. The files include name, national ID number, cell phone number, birthdate, birthplace, ethnicity, education level, marital status, and delivery records. They Read More ›

Could the Self-Checkout Ruin Your Reputation?
As Big Retail’s war on shoplifting goes digital, honest customers risk getting nabbed for goofs — and then facing a shakedownIn 2018, it was noted at The Atlantic that shoplifting via self-serve checkouts was common. How does it work? Self-checkout theft has become so widespread that a whole lingo has sprung up to describe its tactics. Ringing up a T-bone ($13.99/lb) with a code for a cheap ($0.49/lb) variety of produce is “the banana trick.” If a can of Illy espresso leaves the conveyor belt without being scanned, that’s called “the pass around.” “The switcheroo” is more labor-intensive: Peel the sticker off something inexpensive and place it over the bar code of something pricey. Just make sure both items are about the same weight, to avoid triggering that pesky “unexpected item” alert in the bagging area. Rene Chun, “The Banana Read More ›

Can AI Really Predict Crime a Week in Advance? That’s the Claim.
University of Chicago data scientists claim 90% accuracy for their algorithm using past data — but it’s hard to evaluateThe University of Chicago recently announced to great fanfare that, Data and social scientists from the University of Chicago have developed a new algorithm that forecasts crime by learning patterns in time and geographic locations from public data on violent and property crimes. The model can predict future crimes one week in advance with about 90% accuracy. University of Chicago Medical Center, “Algorithm Predicts Crime a Week in Advance, but Reveals Bias in Police Response” at Newswise (June 28, 2022) Many thought immediately of the 2002 movie Minority Report, in which three psychics (“precogs”) visualize murders before they occur, thereby allowing special PreCrime police to arrest would-be assailants before they can commit them. Have these University of Chicago researchers made Read More ›

Are We Losing the Battle With Online Fraud via Deepfakes?
Now, the FBI warns, faked up “tech employees” are applying for remote work jobs with sensitive corporate dataFrom Gizmodo this week we learn that the FBI has received a number of complaints about people using “stolen information and deepfaked video and voice to apply to remote tech jobs”: According to the FBI’s announcement, more companies have been reporting people applying to jobs using video, images, or recordings that are manipulated to look and sound like somebody else. These fakers are also using personal identifiable information from other people—stolen identities—to apply to jobs at IT, programming, database, and software firms. The report noted that many of these open positions had access to sensitive customer or employee data, as well as financial and proprietary company info, implying the imposters could have a desire to steal sensitive information as well Read More ›

The True Cause of Cybersecurity Failure and How to Fix It
Hint: The cause and fix are not what you thinkVeteran software developer David A. Kruger offered some thoughts on computer security recently at Expensivity and we appreciate the opportunity to republish them here. He starts with “Root Cause Analysis 101” The classic line “I have a bad feeling about this” is repeated in every Star Wars movie. It’s become a meme for that uneasy feeling that as bad as things are now, they are about to get much worse. That’s an accurate portrayal of how many of us feel about cybersecurity. Our bad feeling has a sound empirical basis. Yearly cybersecurity losses and loss rates continually increase and never decrease despite annual US cybersecurity expenditures in the tens of billions of dollars and tens of millions of skilled cybersecurity Read More ›

Deepfakes Can Replicate Human Voices Now — Maybe Yours
Digitally faked voice tech has already been used to perpetrate a big bank fraudIt’s not just your face that can be convincingly replicated by a deepfake. It’s also your voice — quite easily as journalist Chloe Beltman found: Given the complexities of speech synthesis, it’s quite a shock to find out just how easy it is to order one up. For a basic conversational build, all a customer has to do is record themselves saying a bunch of scripted lines for roughly an hour. And that’s about it. “We extract 10 to 15 minutes of net recordings for a basic build,” says Speech Morphing founder and CEO Fathy Yassa. The hundreds of phrases I record so that Speech Morphing can build my digital voice double seem very random: “Here the explosion of mirth Read More ›